Vaulting
How Network Tokens Work: Architecture, Flows & Implementation Guide
How Network Tokens Work: Architecture, Flows & Implementation Guide
How Network Tokens Work: Architecture, Flows & Implementation Guide
Nov 22, 2025


Introduction
If you've read our introduction to network tokens, you understand their strategic value for reducing payment failures and improving authorization rates. Now let's get into the technical details that matter for implementation. This guide walks through the complete architecture, stakeholder flows, and practical considerations that payment architects and engineering teams need to successfully deploy network tokenization.
Network tokens aren't just a security upgrade-they're a fundamental shift in how payment data flows through your system. Understanding these flows is crucial whether you're building internal payment infrastructure or evaluating solutions like Hellgate®'s orchestration platform that handles tokenization at the infrastructure layer.
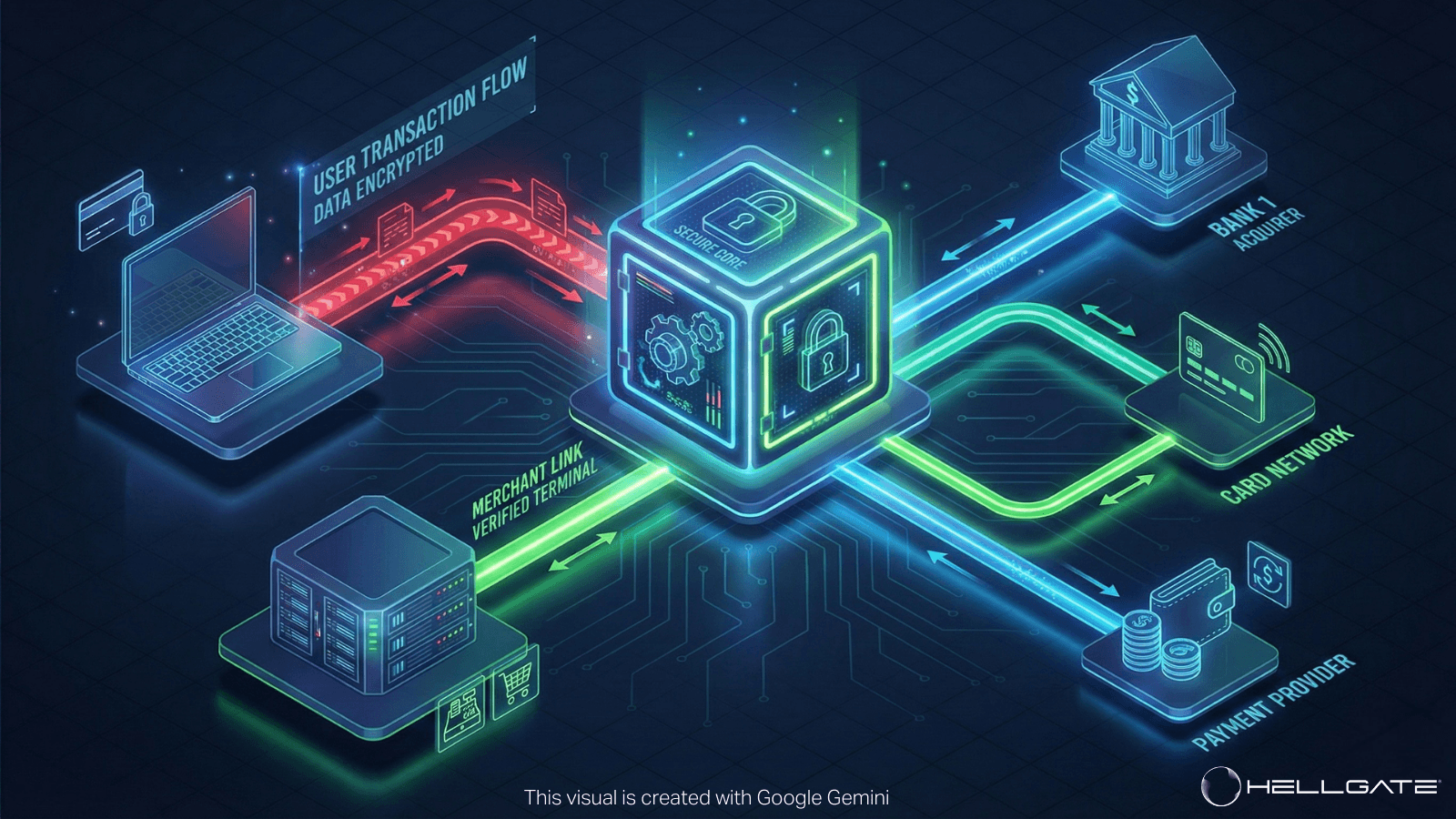
The Network Token Ecosystem: Key Players and Responsibilities
Network tokenization involves multiple stakeholders, each with specific roles in the token lifecycle. Understanding these relationships helps clarify where integration points exist and where potential friction might occur.
Cardholders initiate the process by providing payment credentials during checkout or card-on-file scenarios. From their perspective, the experience should remain seamless-they enter card details once, and future payments work reliably even when their physical card is reissued.
Merchants capture card credentials and manage the customer payment experience. They're responsible for storing tokens securely, handling lifecycle updates, and implementing fallback logic when tokens become unavailable. For recurring billing or subscription models, merchants see the most direct benefit from reduced involuntary churn.
Payment Service Providers (PSPs), gateways, and acquirers handle the technical integration with token service providers. They manage token vaulting, process authorization requests using tokens instead of PANs, and relay lifecycle updates back to merchants. Not all providers support network tokens equally-this becomes a key selection criterion.
Card schemes (Visa, Mastercard, American Express) operate as Token Service Providers (TSPs). They generate tokens, manage lifecycle events, and maintain the mapping between tokens and underlying card accounts. Each scheme has slightly different implementation requirements and capabilities.
Issuing banks participate in token provisioning decisions and trigger lifecycle updates when cards are reissued, suspended, or replaced. Their level of participation varies-some issuers actively manage token lifecycles while others rely primarily on scheme-level automation.
Token Provisioning: From Card to Token
The initial token creation process involves several technical steps that happen largely behind the scenes but require careful orchestration.
When a customer enters card details at checkout, the merchant or PSP initiates a token request to the appropriate card scheme's tokenization service. This request includes the PAN, expiry date, and merchant-specific identifiers like the Token Requestor ID-a unique identifier that ties the token to your specific merchant account.
The card scheme validates the request, often checking with the issuing bank for approval, then generates a network token along with associated metadata. This metadata typically includes a cryptogram for additional security validation and token-specific attributes that define how the token can be used.
The token gets returned to the requesting system, where it's stored in place of or alongside the original PAN. Many merchants maintain both their existing vault tokens and the new network tokens during transition periods, gradually shifting transaction volume to network tokens as confidence builds.
Authorization Flows: How Tokens Move Through Transactions
When processing payments with network tokens, the authorization flow follows familiar patterns with some key differences. Instead of sending the PAN in the authorization request, your system sends the network token along with any associated cryptogram data.
The acquiring bank and card network validate the token, map it back to the underlying card account, and forward the authorization request to the issuer. From the issuer's perspective, they see the original PAN, so existing fraud detection and authorization logic continues to work normally.
This seamless mapping is what enables network tokens to improve authorization rates. The issuer sees a "fresh" card number that hasn't been compromised in data breaches, and the token's cryptogram provides additional validation that the request is legitimate.
For merchants, the key implementation requirement is updating authorization request formatting to include network token data instead of PAN data. Most modern payment APIs handle this transition smoothly, but legacy systems may require more significant updates.
Lifecycle Management: Keeping Tokens Current
One of network tokens' biggest advantages is automated lifecycle management, but this requires merchants to handle various token states and update events properly.
When an underlying card is reissued-whether due to expiration, loss, or suspected fraud-the card scheme automatically updates the associated network token. In many cases, the token itself remains the same, but the associated metadata gets updated to reflect the new card details.
Merchants receive these lifecycle updates through webhook notifications or API polling, depending on their integration approach. The key is building robust logic to handle these updates automatically, ensuring stored payment methods remain valid without customer intervention.
Token states typically include Created, Active, Suspended, and Cancelled. Active tokens process normally, while suspended tokens might work intermittently as issuers evaluate risk. Cancelled tokens require fallback to PAN or prompting customers for updated payment information.
Smart implementations monitor token health proactively, identifying patterns in suspension or cancellation rates that might indicate broader issues with specific card types, issuers, or customer segments.
Technical Architecture Considerations
Several technical nuances significantly impact implementation success and long-term maintainability.
Merchant binding ties network tokens to specific merchant accounts, preventing tokens from being used across different merchants. This reduces fraud risk but creates complexity when switching payment providers. Ensure your token strategy accounts for provider portability requirements.
Cryptogram handling varies by scheme and implementation. Some tokens include dynamic cryptograms that change with each transaction, while others use static validation data. Your authorization logic needs to handle these differences correctly to avoid unnecessary declines.
Cross-processor compatibility becomes crucial for merchants using multiple payment providers or planning future switches. While network tokens are scheme-level constructs, not all processors support them equally. Test token portability during provider evaluation.
Reconciliation and reporting require updates to track which transactions use network tokens versus PANs. This data becomes essential for measuring tokenization impact and optimizing rollout strategies. APIs like Primer's provide cardTokenType indicators to simplify this tracking.
Regional and issuer variation affects token performance significantly. Authorization lift varies by geography, card product type, and issuer participation levels. Plan for gradual rollouts that allow performance measurement across different segments.
Looking Forward: Network Tokens as Strategic Infrastructure
Network tokens represent more than incremental security improvements-they're foundational infrastructure for modern payment systems. As subscription economies grow and embedded finance becomes mainstream, the ability to maintain reliable payment relationships without constant customer intervention becomes increasingly valuable.
The technology continues evolving, with schemes adding new capabilities around real-time lifecycle updates, enhanced fraud detection, and cross-border optimization. Early adopters gain experience managing these capabilities while building competitive advantages in authorization performance and customer experience.
For payment architects and engineering leaders, network tokens offer a clear path toward more resilient, efficient payment infrastructure. The implementation complexity is manageable, the performance benefits are measurable, and the strategic value compounds over time.
At Hellgate®, we've seen how network tokenization integrates with broader payment orchestration strategies to deliver measurable business outcomes. Whether you're building internal capabilities or evaluating platform solutions, treating network tokens as strategic infrastructure rather than optional features typically drives better long-term results.
The question isn't whether to implement network tokens, but how quickly you can do so while maintaining operational excellence and measuring the business impact that justifies the investment.
Introduction
If you've read our introduction to network tokens, you understand their strategic value for reducing payment failures and improving authorization rates. Now let's get into the technical details that matter for implementation. This guide walks through the complete architecture, stakeholder flows, and practical considerations that payment architects and engineering teams need to successfully deploy network tokenization.
Network tokens aren't just a security upgrade-they're a fundamental shift in how payment data flows through your system. Understanding these flows is crucial whether you're building internal payment infrastructure or evaluating solutions like Hellgate®'s orchestration platform that handles tokenization at the infrastructure layer.
The Network Token Ecosystem: Key Players and Responsibilities
Network tokenization involves multiple stakeholders, each with specific roles in the token lifecycle. Understanding these relationships helps clarify where integration points exist and where potential friction might occur.
Cardholders initiate the process by providing payment credentials during checkout or card-on-file scenarios. From their perspective, the experience should remain seamless-they enter card details once, and future payments work reliably even when their physical card is reissued.
Merchants capture card credentials and manage the customer payment experience. They're responsible for storing tokens securely, handling lifecycle updates, and implementing fallback logic when tokens become unavailable. For recurring billing or subscription models, merchants see the most direct benefit from reduced involuntary churn.
Payment Service Providers (PSPs), gateways, and acquirers handle the technical integration with token service providers. They manage token vaulting, process authorization requests using tokens instead of PANs, and relay lifecycle updates back to merchants. Not all providers support network tokens equally-this becomes a key selection criterion.
Card schemes (Visa, Mastercard, American Express) operate as Token Service Providers (TSPs). They generate tokens, manage lifecycle events, and maintain the mapping between tokens and underlying card accounts. Each scheme has slightly different implementation requirements and capabilities.
Issuing banks participate in token provisioning decisions and trigger lifecycle updates when cards are reissued, suspended, or replaced. Their level of participation varies-some issuers actively manage token lifecycles while others rely primarily on scheme-level automation.
Token Provisioning: From Card to Token
The initial token creation process involves several technical steps that happen largely behind the scenes but require careful orchestration.
When a customer enters card details at checkout, the merchant or PSP initiates a token request to the appropriate card scheme's tokenization service. This request includes the PAN, expiry date, and merchant-specific identifiers like the Token Requestor ID-a unique identifier that ties the token to your specific merchant account.
The card scheme validates the request, often checking with the issuing bank for approval, then generates a network token along with associated metadata. This metadata typically includes a cryptogram for additional security validation and token-specific attributes that define how the token can be used.
The token gets returned to the requesting system, where it's stored in place of or alongside the original PAN. Many merchants maintain both their existing vault tokens and the new network tokens during transition periods, gradually shifting transaction volume to network tokens as confidence builds.
Authorization Flows: How Tokens Move Through Transactions
When processing payments with network tokens, the authorization flow follows familiar patterns with some key differences. Instead of sending the PAN in the authorization request, your system sends the network token along with any associated cryptogram data.
The acquiring bank and card network validate the token, map it back to the underlying card account, and forward the authorization request to the issuer. From the issuer's perspective, they see the original PAN, so existing fraud detection and authorization logic continues to work normally.
This seamless mapping is what enables network tokens to improve authorization rates. The issuer sees a "fresh" card number that hasn't been compromised in data breaches, and the token's cryptogram provides additional validation that the request is legitimate.
For merchants, the key implementation requirement is updating authorization request formatting to include network token data instead of PAN data. Most modern payment APIs handle this transition smoothly, but legacy systems may require more significant updates.
Lifecycle Management: Keeping Tokens Current
One of network tokens' biggest advantages is automated lifecycle management, but this requires merchants to handle various token states and update events properly.
When an underlying card is reissued-whether due to expiration, loss, or suspected fraud-the card scheme automatically updates the associated network token. In many cases, the token itself remains the same, but the associated metadata gets updated to reflect the new card details.
Merchants receive these lifecycle updates through webhook notifications or API polling, depending on their integration approach. The key is building robust logic to handle these updates automatically, ensuring stored payment methods remain valid without customer intervention.
Token states typically include Created, Active, Suspended, and Cancelled. Active tokens process normally, while suspended tokens might work intermittently as issuers evaluate risk. Cancelled tokens require fallback to PAN or prompting customers for updated payment information.
Smart implementations monitor token health proactively, identifying patterns in suspension or cancellation rates that might indicate broader issues with specific card types, issuers, or customer segments.
Technical Architecture Considerations
Several technical nuances significantly impact implementation success and long-term maintainability.
Merchant binding ties network tokens to specific merchant accounts, preventing tokens from being used across different merchants. This reduces fraud risk but creates complexity when switching payment providers. Ensure your token strategy accounts for provider portability requirements.
Cryptogram handling varies by scheme and implementation. Some tokens include dynamic cryptograms that change with each transaction, while others use static validation data. Your authorization logic needs to handle these differences correctly to avoid unnecessary declines.
Cross-processor compatibility becomes crucial for merchants using multiple payment providers or planning future switches. While network tokens are scheme-level constructs, not all processors support them equally. Test token portability during provider evaluation.
Reconciliation and reporting require updates to track which transactions use network tokens versus PANs. This data becomes essential for measuring tokenization impact and optimizing rollout strategies. APIs like Primer's provide cardTokenType indicators to simplify this tracking.
Regional and issuer variation affects token performance significantly. Authorization lift varies by geography, card product type, and issuer participation levels. Plan for gradual rollouts that allow performance measurement across different segments.
Looking Forward: Network Tokens as Strategic Infrastructure
Network tokens represent more than incremental security improvements-they're foundational infrastructure for modern payment systems. As subscription economies grow and embedded finance becomes mainstream, the ability to maintain reliable payment relationships without constant customer intervention becomes increasingly valuable.
The technology continues evolving, with schemes adding new capabilities around real-time lifecycle updates, enhanced fraud detection, and cross-border optimization. Early adopters gain experience managing these capabilities while building competitive advantages in authorization performance and customer experience.
For payment architects and engineering leaders, network tokens offer a clear path toward more resilient, efficient payment infrastructure. The implementation complexity is manageable, the performance benefits are measurable, and the strategic value compounds over time.
At Hellgate®, we've seen how network tokenization integrates with broader payment orchestration strategies to deliver measurable business outcomes. Whether you're building internal capabilities or evaluating platform solutions, treating network tokens as strategic infrastructure rather than optional features typically drives better long-term results.
The question isn't whether to implement network tokens, but how quickly you can do so while maintaining operational excellence and measuring the business impact that justifies the investment.
Introduction
If you've read our introduction to network tokens, you understand their strategic value for reducing payment failures and improving authorization rates. Now let's get into the technical details that matter for implementation. This guide walks through the complete architecture, stakeholder flows, and practical considerations that payment architects and engineering teams need to successfully deploy network tokenization.
Network tokens aren't just a security upgrade-they're a fundamental shift in how payment data flows through your system. Understanding these flows is crucial whether you're building internal payment infrastructure or evaluating solutions like Hellgate®'s orchestration platform that handles tokenization at the infrastructure layer.
The Network Token Ecosystem: Key Players and Responsibilities
Network tokenization involves multiple stakeholders, each with specific roles in the token lifecycle. Understanding these relationships helps clarify where integration points exist and where potential friction might occur.
Cardholders initiate the process by providing payment credentials during checkout or card-on-file scenarios. From their perspective, the experience should remain seamless-they enter card details once, and future payments work reliably even when their physical card is reissued.
Merchants capture card credentials and manage the customer payment experience. They're responsible for storing tokens securely, handling lifecycle updates, and implementing fallback logic when tokens become unavailable. For recurring billing or subscription models, merchants see the most direct benefit from reduced involuntary churn.
Payment Service Providers (PSPs), gateways, and acquirers handle the technical integration with token service providers. They manage token vaulting, process authorization requests using tokens instead of PANs, and relay lifecycle updates back to merchants. Not all providers support network tokens equally-this becomes a key selection criterion.
Card schemes (Visa, Mastercard, American Express) operate as Token Service Providers (TSPs). They generate tokens, manage lifecycle events, and maintain the mapping between tokens and underlying card accounts. Each scheme has slightly different implementation requirements and capabilities.
Issuing banks participate in token provisioning decisions and trigger lifecycle updates when cards are reissued, suspended, or replaced. Their level of participation varies-some issuers actively manage token lifecycles while others rely primarily on scheme-level automation.
Token Provisioning: From Card to Token
The initial token creation process involves several technical steps that happen largely behind the scenes but require careful orchestration.
When a customer enters card details at checkout, the merchant or PSP initiates a token request to the appropriate card scheme's tokenization service. This request includes the PAN, expiry date, and merchant-specific identifiers like the Token Requestor ID-a unique identifier that ties the token to your specific merchant account.
The card scheme validates the request, often checking with the issuing bank for approval, then generates a network token along with associated metadata. This metadata typically includes a cryptogram for additional security validation and token-specific attributes that define how the token can be used.
The token gets returned to the requesting system, where it's stored in place of or alongside the original PAN. Many merchants maintain both their existing vault tokens and the new network tokens during transition periods, gradually shifting transaction volume to network tokens as confidence builds.
Authorization Flows: How Tokens Move Through Transactions
When processing payments with network tokens, the authorization flow follows familiar patterns with some key differences. Instead of sending the PAN in the authorization request, your system sends the network token along with any associated cryptogram data.
The acquiring bank and card network validate the token, map it back to the underlying card account, and forward the authorization request to the issuer. From the issuer's perspective, they see the original PAN, so existing fraud detection and authorization logic continues to work normally.
This seamless mapping is what enables network tokens to improve authorization rates. The issuer sees a "fresh" card number that hasn't been compromised in data breaches, and the token's cryptogram provides additional validation that the request is legitimate.
For merchants, the key implementation requirement is updating authorization request formatting to include network token data instead of PAN data. Most modern payment APIs handle this transition smoothly, but legacy systems may require more significant updates.
Lifecycle Management: Keeping Tokens Current
One of network tokens' biggest advantages is automated lifecycle management, but this requires merchants to handle various token states and update events properly.
When an underlying card is reissued-whether due to expiration, loss, or suspected fraud-the card scheme automatically updates the associated network token. In many cases, the token itself remains the same, but the associated metadata gets updated to reflect the new card details.
Merchants receive these lifecycle updates through webhook notifications or API polling, depending on their integration approach. The key is building robust logic to handle these updates automatically, ensuring stored payment methods remain valid without customer intervention.
Token states typically include Created, Active, Suspended, and Cancelled. Active tokens process normally, while suspended tokens might work intermittently as issuers evaluate risk. Cancelled tokens require fallback to PAN or prompting customers for updated payment information.
Smart implementations monitor token health proactively, identifying patterns in suspension or cancellation rates that might indicate broader issues with specific card types, issuers, or customer segments.
Technical Architecture Considerations
Several technical nuances significantly impact implementation success and long-term maintainability.
Merchant binding ties network tokens to specific merchant accounts, preventing tokens from being used across different merchants. This reduces fraud risk but creates complexity when switching payment providers. Ensure your token strategy accounts for provider portability requirements.
Cryptogram handling varies by scheme and implementation. Some tokens include dynamic cryptograms that change with each transaction, while others use static validation data. Your authorization logic needs to handle these differences correctly to avoid unnecessary declines.
Cross-processor compatibility becomes crucial for merchants using multiple payment providers or planning future switches. While network tokens are scheme-level constructs, not all processors support them equally. Test token portability during provider evaluation.
Reconciliation and reporting require updates to track which transactions use network tokens versus PANs. This data becomes essential for measuring tokenization impact and optimizing rollout strategies. APIs like Primer's provide cardTokenType indicators to simplify this tracking.
Regional and issuer variation affects token performance significantly. Authorization lift varies by geography, card product type, and issuer participation levels. Plan for gradual rollouts that allow performance measurement across different segments.
Looking Forward: Network Tokens as Strategic Infrastructure
Network tokens represent more than incremental security improvements-they're foundational infrastructure for modern payment systems. As subscription economies grow and embedded finance becomes mainstream, the ability to maintain reliable payment relationships without constant customer intervention becomes increasingly valuable.
The technology continues evolving, with schemes adding new capabilities around real-time lifecycle updates, enhanced fraud detection, and cross-border optimization. Early adopters gain experience managing these capabilities while building competitive advantages in authorization performance and customer experience.
For payment architects and engineering leaders, network tokens offer a clear path toward more resilient, efficient payment infrastructure. The implementation complexity is manageable, the performance benefits are measurable, and the strategic value compounds over time.
At Hellgate®, we've seen how network tokenization integrates with broader payment orchestration strategies to deliver measurable business outcomes. Whether you're building internal capabilities or evaluating platform solutions, treating network tokens as strategic infrastructure rather than optional features typically drives better long-term results.
The question isn't whether to implement network tokens, but how quickly you can do so while maintaining operational excellence and measuring the business impact that justifies the investment.
Co-Founder & Chief of Revenue and growth at Starfish & Co. – creators of Hellgate®
Co-Founder & Chief of Revenue and growth at Starfish & Co. – creators of Hellgate®
Jens Kohnen was driven to co-start the company by the conviction that payment infrastructure should empower businesses, not bind them. Recognizing that many large organizations were locked into monolithic, opaque setups, Jens embarked on a journey to free enterprises from these rigid stacks. His mission is to enable companies to regain full ownership and monetize their flows, transforming payments from a cost center into a strategic lever for growth.
Vaulting
Feb 9, 2026
Beyond the Walled Garden: Architecting a Sovereign Payment Stack

Vaulting
Feb 9, 2026
Beyond the Walled Garden: Architecting a Sovereign Payment Stack

Vaulting
Feb 9, 2026
Beyond the Walled Garden: Architecting a Sovereign Payment Stack

Vaulting
Jan 15, 2026
Tokenization as a Service: The Infrastructure-First Approach to Data Security

Vaulting
Jan 15, 2026
Tokenization as a Service: The Infrastructure-First Approach to Data Security

Vaulting
Jan 15, 2026
Tokenization as a Service: The Infrastructure-First Approach to Data Security

Vaulting
Jan 9, 2026
Beyond the PSP: Choosing the Right Payment Tokenization Service Provider

Vaulting
Jan 9, 2026
Beyond the PSP: Choosing the Right Payment Tokenization Service Provider

Vaulting
Jan 9, 2026
Beyond the PSP: Choosing the Right Payment Tokenization Service Provider
See Hellgate CPA in action
Let our product specialists guide you through the platform, touch upon all functionalities relevant for your individual use case and answer all your questions directly.
See Hellgate CPA in action
Let our product specialists guide you through the platform, touch upon all functionalities relevant for your individual use case and answer all your questions directly.
See Hellgate CPA in action
Let our product specialists guide you through the platform, touch upon all functionalities relevant for your individual use case and answer all your questions directly.



