T
C
Card Data Vaulting
Card Data Vaulting
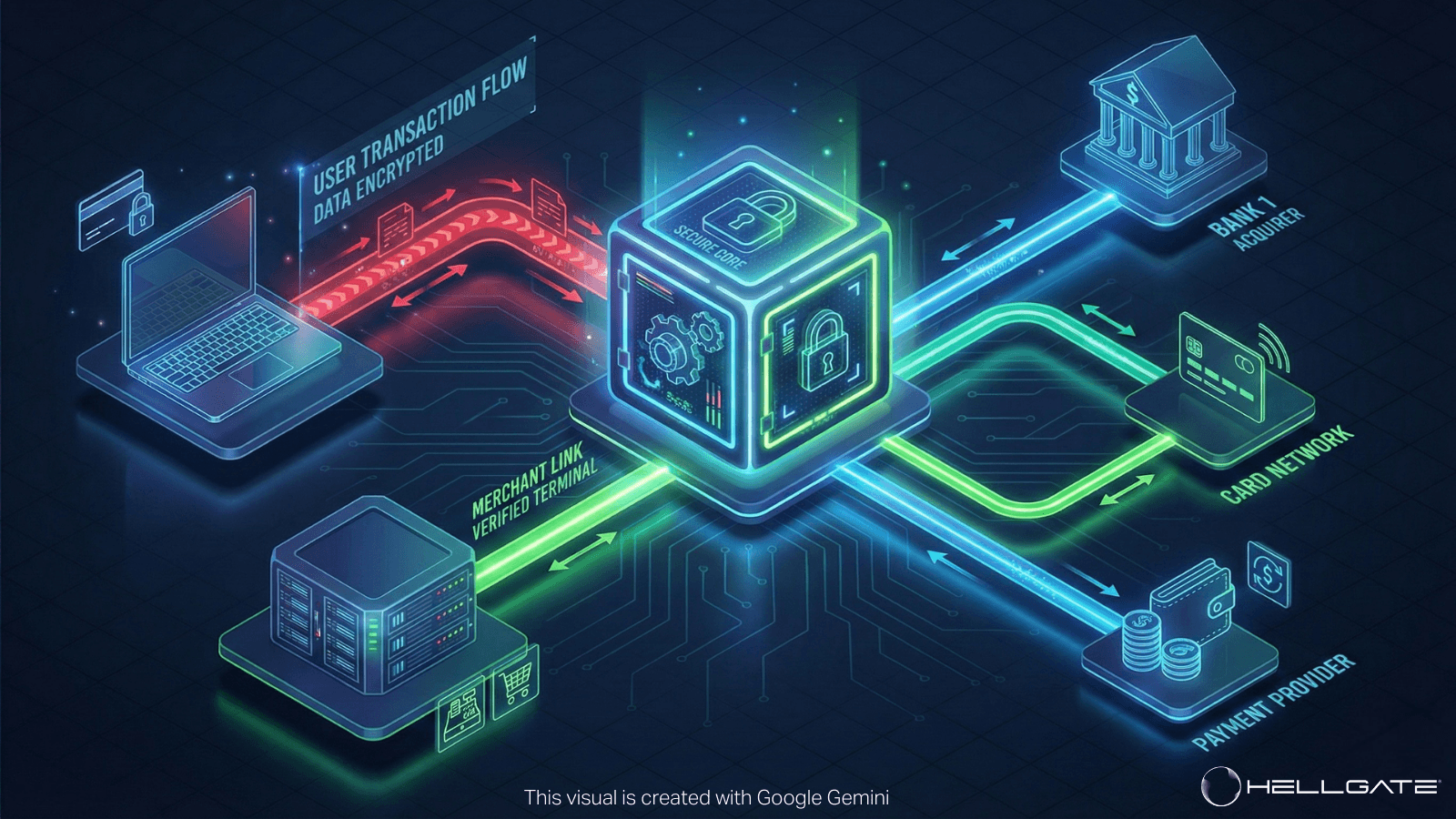
Card Data Vaulting is the process of capturing, encrypting, and storing sensitive payment information (such as Primary Account Numbers or PANs) in a secure, PCI-compliant environment separate from the merchant's core infrastructure. Instead of storing the raw card data, the vault generates a non-sensitive "token"—a random string of alphanumeric characters—that serves as a reference ID for future transactions. This allows merchants to initiate payments without ever handling or exposing the actual card details.
Deep Dive: The Mechanics of Secure Storage
1. Technical Architecture: Vaulted vs. Vaultless
While the end result (a token) is the same, the backend architecture of a vault can differ significantly, impacting performance and scalability:
Vaulted Tokenization (Database-Driven): The traditional method. The system maintains a secure database (the "vault") that maps the original PAN to the generated token. When a transaction occurs, the system looks up the token in the database to retrieve the PAN for processing. This allows for specific numeric token formats but introduces database latency and replication requirements for disaster recovery.
Vaultless Tokenization (Algorithmic): A modern approach where the token is generated via a reversible, format-preserving encryption algorithm. No central database maps the token to the PAN; instead, the token is the encrypted data. This reduces latency (no database lookups) and simplifies scaling since there is no centralized vault to replicate.
2. Strategic Importance: Independence & Agility
For CTOs, the location of the vault is a strategic decision that defines the flexibility of the entire payment stack.
PSP Vaults (The Trap): When a merchant uses a Payment Service Provider's (PSP) built-in vault (e.g., saving a card on Stripe), that token is proprietary. It cannot be used by another provider. If the merchant wants to switch to a cheaper provider, they cannot migrate the tokens easily, leading to "Vendor Lock-in."
Independent Vaults (The Solution): An agnostic vault sits above the PSP layer. It tokenizes the card once and allows the merchant to route that transaction to any connected provider. The merchant owns the token, not the PSP.
3. Implementation Challenges
Latency: The vault adds a step to the transaction flow (Detokenization -> Send to PSP). High-performance infrastructure is required to ensure this adds negligible latency.
PCI DSS Compliance: While vaulting reduces the merchant's scope (often to SAQ-A), the vault provider itself must maintain the highest level of compliance (PCI DSS Level 1).
Common Pain Points
Failing to implement an independent vaulting strategy creates significant friction:
Vendor Lock-In: Migrating card-on-file data from one PSP to another is notoriously difficult, expensive, and often results in customer churn (users forced to re-enter cards).
Routing Limitations: Without an agnostic vault, you cannot implement Smart Routing. You cannot route a "Stripe Token" to "Adyen" to save on fees; you are forced to process it where it was stored.
Compliance Burden: Storing PANs internally (even encrypted) brings the merchant's entire network into full PCI scope, necessitating expensive annual audits.
The Hellgate Approach
In the Hellgate CPA framework, card data vaulting is handled by the Guardian module, which serves as a provider-agnostic security layer.
Universal Tokenization: Guardian captures the PAN at the point of entry (via hosted fields) and issues a Universal Token. This token allows the Hub (Orchestration) to route the transaction to any connected acquirer, effectively decoupling the storage of data from the processing of data.
Network Tokens: Beyond standard vaulting, Guardian supports Network Tokenization. Instead of just creating a static proxy token, Guardian requests a Scheme Token directly from Visa/Mastercard. These tokens automatically update if the physical card expires or is replaced (Lifecycle Management), significantly increasing authorization rates for recurring billing.
Scope Descoping: By intercepting the data before it touches the merchant's backend, Guardian reduces the merchant's compliance burden to the absolute minimum.
FAQ
Question: What is the difference between Tokenization and Encryption?
Answer: Encryption protects data by scrambling it with a key (which can be reversed if the key is stolen). Tokenization replaces the data entirely with a non-sensitive placeholder. If a database of tokens is stolen, they are useless to a hacker because they cannot be mathematically reversed to reveal the original card number.
Question: Can I switch PSPs if I use a PSP's internal vault?
Answer: Technically yes, but it is painful. You must request a "Data Migration" where the old PSP transfers the raw PANs to the new PSP. This process is slow, costly, and often results in data loss (failed transfers), forcing customers to re-enter their payment details.
Question: Does Card Vaulting support recurring payments?
Answer: Yes. Vaulting is the foundation of the "Card-on-File" model. The merchant stores the token and calls it repeatedly for subscription renewals or one-click checkouts without asking the customer for data again.