Vaulting
Token Service Provider: A Guide to Tokenization in Digital Payments
Token Service Provider: A Guide to Tokenization in Digital Payments
Token Service Provider: A Guide to Tokenization in Digital Payments
Nov 8, 2025


The payment landscape has fundamentally shifted. What used to be straightforward card-present transactions have evolved into complex digital ecosystems where sensitive payment data moves across multiple touchpoints, third-party services, and geographic boundaries. For enterprise payment teams, this complexity brings both opportunity and risk.
Consider this reality: the average enterprise payment flows through 5-7 different systems before completion. Each touchpoint represents a potential vulnerability where sensitive cardholder data could be exposed, stolen, or mishandled. The cost of a single data breach now averages $4.45 million, with payment card data breaches often carrying the highest remediation costs.
This is where tokenization and token service providers become critical infrastructure rather than nice-to-have security features. But understanding how tokenization actually works, who provides these services, and how to implement them effectively requires cutting through significant technical complexity.
What is a Token Service Provider?
A token service provider (TSP) is a specialized entity that replaces sensitive payment data with non-sensitive tokens, creating a secure barrier between your systems and actual cardholder information. Think of it as a sophisticated translation service that converts valuable data into meaningless substitutes while maintaining the ability to reverse the process when legitimate payment processing is required.
The token itself is typically a randomly generated string of characters that matches the format of the original data but holds no intrinsic value. If intercepted, stolen, or accidentally exposed, tokens are useless to bad actors because they cannot be reverse-engineered or used for fraudulent transactions outside the specific tokenization system that created them.
Here's what makes token service providers particularly valuable for enterprise operations: they operate as trusted intermediaries that can securely store and manage the mapping between tokens and real payment data. This means your internal systems, third-party integrations, analytics platforms, and reporting tools can all work with tokenized data while the actual sensitive information remains isolated in a highly secure environment.
Token service providers typically offer different types of tokenization depending on your specific use case. Format-preserving tokens maintain the same structure as original payment data, making them ideal for legacy systems that expect specific data formats. Non-format-preserving tokens offer maximum security but may require system modifications to handle different data structures.
How a Token Service Provider Works
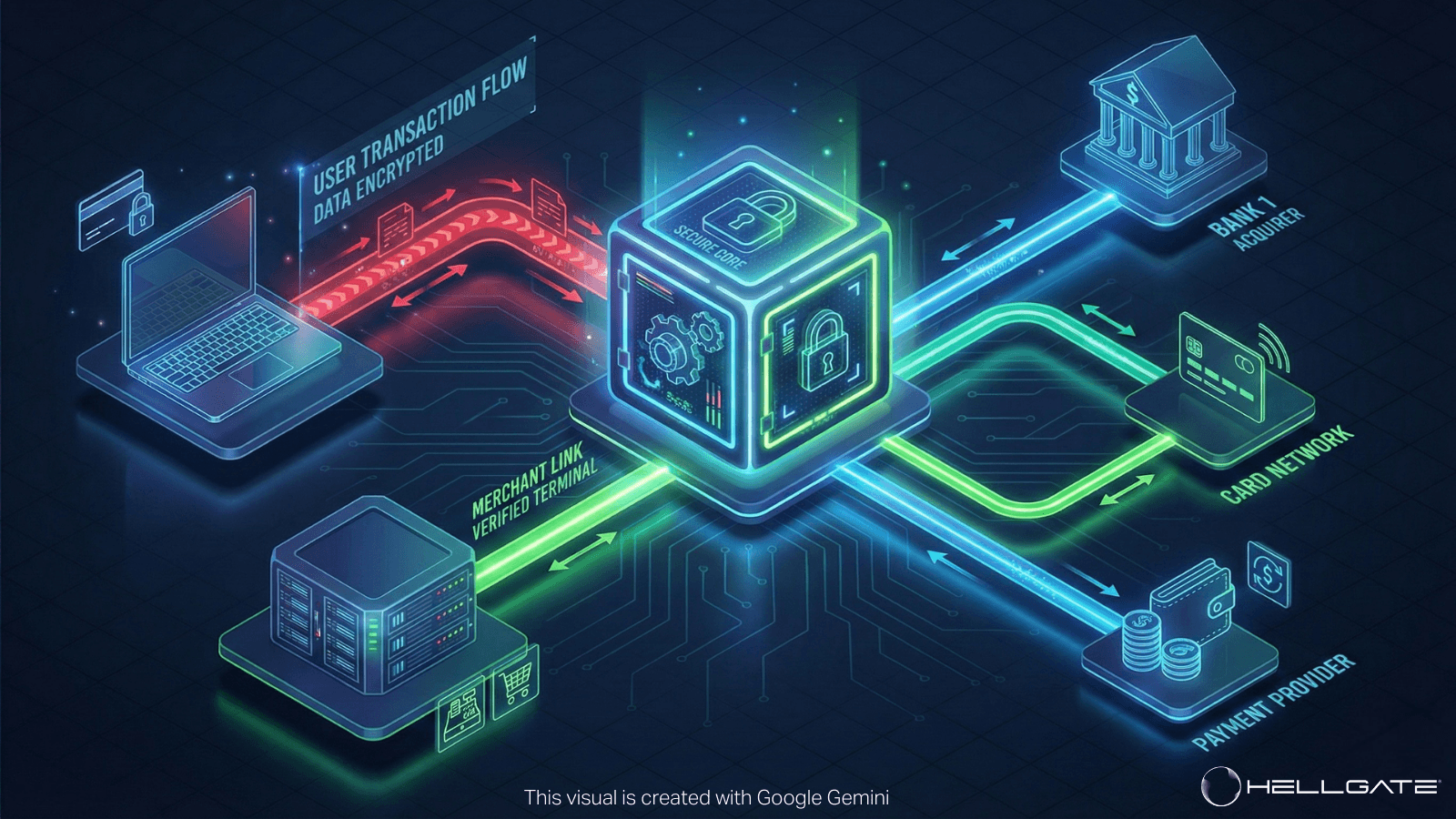
The tokenization process involves several sophisticated steps that happen seamlessly in the background of your payment operations. Understanding this flow helps enterprise teams make better architectural decisions and troubleshoot integration challenges.
When a customer initiates a payment, their sensitive card data first enters your system through whatever channel they're using - your website, mobile app, point-of-sale system, or API integration. Instead of storing or processing this data directly, your system immediately sends it to your token service provider through a secure API call.
The token service provider receives this sensitive data and performs several critical operations simultaneously. First, it generates a unique token using cryptographically secure random number generation. This token is designed to be statistically unique across your entire token population, preventing collisions or predictable patterns that could create security vulnerabilities.
Next, the provider securely stores the mapping between the original data and the new token in what's often called a token vault. This vault represents the most heavily secured component of the entire system, typically featuring multiple layers of encryption, access controls, audit logging, and physical security measures that exceed most enterprise security capabilities.
The token is then returned to your system, where it can be safely stored, processed, and transmitted just like any other piece of non-sensitive data. Your existing workflows, reporting systems, customer service tools, and analytics platforms can all work with tokens without requiring significant modifications or additional security measures.
When you actually need to process a payment, your system sends the token back to the token service provider along with your processing request. The provider retrieves the original payment data, forwards it to the appropriate payment processor or network, and returns the processing results to your system - all while ensuring the sensitive data never re-enters your environment.
This architecture creates what security professionals call "data segmentation" - a clear boundary between systems that handle sensitive data and those that don't. Most of your infrastructure operates in the token environment, while only the token service provider and payment processors work with actual cardholder data.
Who Needs a Token Service Provider?
The short answer is any organization that handles payment data and wants to minimize security risks while maintaining operational flexibility. But the longer answer reveals specific scenarios where token service providers become particularly valuable for enterprise operations.
E-commerce platforms and marketplaces face unique challenges because they often need to store payment information for future transactions, subscription billing, or marketplace payouts. Without tokenization, storing this data creates significant PCI DSS compliance burdens and security risks. Token service providers allow these businesses to maintain all their customer experience features while dramatically reducing their compliance scope.
Subscription and recurring billing businesses represent another critical use case. These companies need to process payments on ongoing schedules, handle plan changes, manage failed payment recovery, and provide customer service access to payment information. Tokenization enables all these operations while ensuring that payment data remains secure even if internal systems are compromised.
Multi-channel retailers operating both online and offline face particular complexity because payment data often needs to flow between different systems, locations, and operational contexts. A customer might save a payment method online, use it for in-store pickup, and later apply it to a mobile app purchase. Token service providers enable this seamless experience while maintaining security across all channels.
B2B companies with complex payment workflows often discover that tokenization solves problems they didn't initially recognize. When payment data needs to flow through approval workflows, accounting systems, customer relationship management platforms, and reporting tools, tokenization ensures that all these systems can operate normally without creating security vulnerabilities.
Companies expanding internationally face additional regulatory complexity as different regions impose varying requirements for payment data handling. Token service providers can help navigate these requirements by ensuring that sensitive data storage and processing occur in appropriate jurisdictions while allowing business operations to continue normally.
Perhaps most importantly, any organization dealing with third-party integrations should seriously consider tokenization. Whether you're working with analytics providers, customer service platforms, marketing automation tools, or business intelligence systems, tokenization allows you to share operational data without exposing sensitive payment information.
Key Benefits of Using a Token Service Provider
The primary benefit that drives most enterprise adoption is dramatic PCI DSS scope reduction. When your systems only handle tokens rather than actual payment data, large portions of your infrastructure fall outside PCI compliance requirements. This translates directly into reduced compliance costs, simpler audit processes, and lower ongoing security maintenance overhead.
But scope reduction is just the beginning. Token service providers enable operational flexibility that would be difficult or impossible to achieve while maintaining direct control over sensitive payment data. You can integrate with new third-party services, expand into new markets, experiment with different payment flows, and modify internal processes without constantly evaluating security implications.
Security improvements extend beyond compliance requirements. Even if your internal systems are compromised, tokenized data provides no value to attackers. This creates multiple layers of protection and significantly reduces the potential impact of security incidents. Many enterprises find that tokenization enables them to be more aggressive with innovation and system integration because the security risks are fundamentally different.
Operational efficiency gains often surprise enterprise teams. When you don't need to treat every piece of payment-related data as highly sensitive, reporting becomes simpler, customer service becomes more effective, and system integration becomes faster. Teams can focus on business logic rather than security implementation, leading to faster development cycles and more reliable systems.
Token service providers also enable advanced payment orchestration strategies that would be complex to implement securely otherwise. You can route payments through different processors based on various criteria, implement sophisticated retry logic, and optimize for cost or performance without exposing sensitive data to multiple external systems.
What Should I Look for When Choosing a Token Service Provider?
Several critical factors should guide your token service provider selection, each carrying significant implications for your long-term payment infrastructure success.
Direct Network Connections
Direct connectivity becomes essential when your operations involve latency-sensitive transactions, high data volumes, or regulated environments. Look for providers that maintain direct relationships with payment networks rather than relying on intermediary connections. This direct access typically translates into better performance, more reliable service, and enhanced security controls that matter at enterprise scale.
Security Capabilities
Your token service provider must demonstrate comprehensive security capabilities that go beyond basic tokenization. Robust tokenization methods should include format-preserving options when needed, while encryption standards like AES-256 provide the foundation for data protection. Comprehensive key management capabilities become particularly important, with the best providers allowing you to maintain control over your encryption keys when required.
Role-based access controls ensure that only authorized personnel can access sensitive functions, while detailed audit logs provide the accountability and traceability that enterprise security teams require. These capabilities aren't just nice-to-have features - they're essential components of a security architecture that can withstand sophisticated attacks.
Interoperability and Integration
Your token service provider should integrate seamlessly into your existing technology ecosystem without forcing expensive modifications or creating operational friction. Well-documented APIs and SDKs in common programming languages accelerate implementation and reduce ongoing maintenance overhead.
Support for both batch and real-time operations provides flexibility for different use cases within your organization. Some processes may require immediate tokenization, while others can benefit from efficient batch processing. Flexible token formats and compatibility with your databases, cloud platforms, and SaaS applications ensure smooth deployment across your entire technology stack.
Compliance Support
Compliance with industry standards such as PCI DSS, GDPR, HIPAA, and SOC 2 represents the baseline expectation rather than a differentiating feature. However, the depth and sophistication of compliance support varies significantly between providers.
Look for features like configurable data residency that allows you to meet regional regulatory requirements, detailed audit logging that supports compliance reporting, and regular third-party security assessments that validate the provider's security practices. The best providers treat compliance as an ongoing commitment rather than a one-time certification.
Performance, Scalability, and Availability
As your business grows, your tokenization solution must scale proportionally without degrading performance or reliability. High-throughput capabilities become critical for enterprises processing large transaction volumes, while support for both real-time and batch operations provides operational flexibility.
High availability through globally distributed infrastructure and built-in redundancy ensures that tokenization services remain accessible even during regional outages or maintenance windows. SLA-backed performance guarantees provide the assurance that mission-critical systems require, with clear remediation processes when performance standards aren't met.
Is Hellgate® Guardian a Token Service Provider?
Yes, Hellgate® Guardian is a leading independent token service provider that offers robust data tokenization, replacing sensitive data such as card numbers with format-preserving tokens. These tokens can be used throughout your systems without exposing the original data, creating a secure operational environment that maintains full functionality.
Guardian stands out as one of the only PSP-agnostic token service providers in the market. This independence allows merchants and enterprises to tokenize payment card data and manage tokens without being locked into a specific payment processing partner. Card data is stored and tokenized in a centralized, secure environment that remains accessible regardless of the processing channel you choose.
Guardian provides a secure vault that stores sensitive data off your infrastructure, dramatically reducing your PCI DSS compliance scope. Beyond vaulting capabilities, Guardian acts as a PCI-compliant proxy, helping businesses collect, store, and exchange sensitive data without ever seeing or storing it directly within their own systems.
With direct connections to all leading card networks - Visa, Mastercard, Discover, and American Express - Guardian gives businesses greater control over their tokenization and vaulting strategies. This comprehensive network connectivity is especially valuable when you want to remain payment processor-agnostic while maintaining the highest levels of security and performance.
The combination of independent operation, comprehensive network connectivity, and advanced security capabilities makes Guardian particularly well-suited for enterprises that need flexible, scalable tokenization solutions without vendor lock-in constraints.
The payment landscape has fundamentally shifted. What used to be straightforward card-present transactions have evolved into complex digital ecosystems where sensitive payment data moves across multiple touchpoints, third-party services, and geographic boundaries. For enterprise payment teams, this complexity brings both opportunity and risk.
Consider this reality: the average enterprise payment flows through 5-7 different systems before completion. Each touchpoint represents a potential vulnerability where sensitive cardholder data could be exposed, stolen, or mishandled. The cost of a single data breach now averages $4.45 million, with payment card data breaches often carrying the highest remediation costs.
This is where tokenization and token service providers become critical infrastructure rather than nice-to-have security features. But understanding how tokenization actually works, who provides these services, and how to implement them effectively requires cutting through significant technical complexity.
What is a Token Service Provider?
A token service provider (TSP) is a specialized entity that replaces sensitive payment data with non-sensitive tokens, creating a secure barrier between your systems and actual cardholder information. Think of it as a sophisticated translation service that converts valuable data into meaningless substitutes while maintaining the ability to reverse the process when legitimate payment processing is required.
The token itself is typically a randomly generated string of characters that matches the format of the original data but holds no intrinsic value. If intercepted, stolen, or accidentally exposed, tokens are useless to bad actors because they cannot be reverse-engineered or used for fraudulent transactions outside the specific tokenization system that created them.
Here's what makes token service providers particularly valuable for enterprise operations: they operate as trusted intermediaries that can securely store and manage the mapping between tokens and real payment data. This means your internal systems, third-party integrations, analytics platforms, and reporting tools can all work with tokenized data while the actual sensitive information remains isolated in a highly secure environment.
Token service providers typically offer different types of tokenization depending on your specific use case. Format-preserving tokens maintain the same structure as original payment data, making them ideal for legacy systems that expect specific data formats. Non-format-preserving tokens offer maximum security but may require system modifications to handle different data structures.
How a Token Service Provider Works
The tokenization process involves several sophisticated steps that happen seamlessly in the background of your payment operations. Understanding this flow helps enterprise teams make better architectural decisions and troubleshoot integration challenges.
When a customer initiates a payment, their sensitive card data first enters your system through whatever channel they're using - your website, mobile app, point-of-sale system, or API integration. Instead of storing or processing this data directly, your system immediately sends it to your token service provider through a secure API call.
The token service provider receives this sensitive data and performs several critical operations simultaneously. First, it generates a unique token using cryptographically secure random number generation. This token is designed to be statistically unique across your entire token population, preventing collisions or predictable patterns that could create security vulnerabilities.
Next, the provider securely stores the mapping between the original data and the new token in what's often called a token vault. This vault represents the most heavily secured component of the entire system, typically featuring multiple layers of encryption, access controls, audit logging, and physical security measures that exceed most enterprise security capabilities.
The token is then returned to your system, where it can be safely stored, processed, and transmitted just like any other piece of non-sensitive data. Your existing workflows, reporting systems, customer service tools, and analytics platforms can all work with tokens without requiring significant modifications or additional security measures.
When you actually need to process a payment, your system sends the token back to the token service provider along with your processing request. The provider retrieves the original payment data, forwards it to the appropriate payment processor or network, and returns the processing results to your system - all while ensuring the sensitive data never re-enters your environment.
This architecture creates what security professionals call "data segmentation" - a clear boundary between systems that handle sensitive data and those that don't. Most of your infrastructure operates in the token environment, while only the token service provider and payment processors work with actual cardholder data.
Who Needs a Token Service Provider?
The short answer is any organization that handles payment data and wants to minimize security risks while maintaining operational flexibility. But the longer answer reveals specific scenarios where token service providers become particularly valuable for enterprise operations.
E-commerce platforms and marketplaces face unique challenges because they often need to store payment information for future transactions, subscription billing, or marketplace payouts. Without tokenization, storing this data creates significant PCI DSS compliance burdens and security risks. Token service providers allow these businesses to maintain all their customer experience features while dramatically reducing their compliance scope.
Subscription and recurring billing businesses represent another critical use case. These companies need to process payments on ongoing schedules, handle plan changes, manage failed payment recovery, and provide customer service access to payment information. Tokenization enables all these operations while ensuring that payment data remains secure even if internal systems are compromised.
Multi-channel retailers operating both online and offline face particular complexity because payment data often needs to flow between different systems, locations, and operational contexts. A customer might save a payment method online, use it for in-store pickup, and later apply it to a mobile app purchase. Token service providers enable this seamless experience while maintaining security across all channels.
B2B companies with complex payment workflows often discover that tokenization solves problems they didn't initially recognize. When payment data needs to flow through approval workflows, accounting systems, customer relationship management platforms, and reporting tools, tokenization ensures that all these systems can operate normally without creating security vulnerabilities.
Companies expanding internationally face additional regulatory complexity as different regions impose varying requirements for payment data handling. Token service providers can help navigate these requirements by ensuring that sensitive data storage and processing occur in appropriate jurisdictions while allowing business operations to continue normally.
Perhaps most importantly, any organization dealing with third-party integrations should seriously consider tokenization. Whether you're working with analytics providers, customer service platforms, marketing automation tools, or business intelligence systems, tokenization allows you to share operational data without exposing sensitive payment information.
Key Benefits of Using a Token Service Provider
The primary benefit that drives most enterprise adoption is dramatic PCI DSS scope reduction. When your systems only handle tokens rather than actual payment data, large portions of your infrastructure fall outside PCI compliance requirements. This translates directly into reduced compliance costs, simpler audit processes, and lower ongoing security maintenance overhead.
But scope reduction is just the beginning. Token service providers enable operational flexibility that would be difficult or impossible to achieve while maintaining direct control over sensitive payment data. You can integrate with new third-party services, expand into new markets, experiment with different payment flows, and modify internal processes without constantly evaluating security implications.
Security improvements extend beyond compliance requirements. Even if your internal systems are compromised, tokenized data provides no value to attackers. This creates multiple layers of protection and significantly reduces the potential impact of security incidents. Many enterprises find that tokenization enables them to be more aggressive with innovation and system integration because the security risks are fundamentally different.
Operational efficiency gains often surprise enterprise teams. When you don't need to treat every piece of payment-related data as highly sensitive, reporting becomes simpler, customer service becomes more effective, and system integration becomes faster. Teams can focus on business logic rather than security implementation, leading to faster development cycles and more reliable systems.
Token service providers also enable advanced payment orchestration strategies that would be complex to implement securely otherwise. You can route payments through different processors based on various criteria, implement sophisticated retry logic, and optimize for cost or performance without exposing sensitive data to multiple external systems.
What Should I Look for When Choosing a Token Service Provider?
Several critical factors should guide your token service provider selection, each carrying significant implications for your long-term payment infrastructure success.
Direct Network Connections
Direct connectivity becomes essential when your operations involve latency-sensitive transactions, high data volumes, or regulated environments. Look for providers that maintain direct relationships with payment networks rather than relying on intermediary connections. This direct access typically translates into better performance, more reliable service, and enhanced security controls that matter at enterprise scale.
Security Capabilities
Your token service provider must demonstrate comprehensive security capabilities that go beyond basic tokenization. Robust tokenization methods should include format-preserving options when needed, while encryption standards like AES-256 provide the foundation for data protection. Comprehensive key management capabilities become particularly important, with the best providers allowing you to maintain control over your encryption keys when required.
Role-based access controls ensure that only authorized personnel can access sensitive functions, while detailed audit logs provide the accountability and traceability that enterprise security teams require. These capabilities aren't just nice-to-have features - they're essential components of a security architecture that can withstand sophisticated attacks.
Interoperability and Integration
Your token service provider should integrate seamlessly into your existing technology ecosystem without forcing expensive modifications or creating operational friction. Well-documented APIs and SDKs in common programming languages accelerate implementation and reduce ongoing maintenance overhead.
Support for both batch and real-time operations provides flexibility for different use cases within your organization. Some processes may require immediate tokenization, while others can benefit from efficient batch processing. Flexible token formats and compatibility with your databases, cloud platforms, and SaaS applications ensure smooth deployment across your entire technology stack.
Compliance Support
Compliance with industry standards such as PCI DSS, GDPR, HIPAA, and SOC 2 represents the baseline expectation rather than a differentiating feature. However, the depth and sophistication of compliance support varies significantly between providers.
Look for features like configurable data residency that allows you to meet regional regulatory requirements, detailed audit logging that supports compliance reporting, and regular third-party security assessments that validate the provider's security practices. The best providers treat compliance as an ongoing commitment rather than a one-time certification.
Performance, Scalability, and Availability
As your business grows, your tokenization solution must scale proportionally without degrading performance or reliability. High-throughput capabilities become critical for enterprises processing large transaction volumes, while support for both real-time and batch operations provides operational flexibility.
High availability through globally distributed infrastructure and built-in redundancy ensures that tokenization services remain accessible even during regional outages or maintenance windows. SLA-backed performance guarantees provide the assurance that mission-critical systems require, with clear remediation processes when performance standards aren't met.
Is Hellgate® Guardian a Token Service Provider?
Yes, Hellgate® Guardian is a leading independent token service provider that offers robust data tokenization, replacing sensitive data such as card numbers with format-preserving tokens. These tokens can be used throughout your systems without exposing the original data, creating a secure operational environment that maintains full functionality.
Guardian stands out as one of the only PSP-agnostic token service providers in the market. This independence allows merchants and enterprises to tokenize payment card data and manage tokens without being locked into a specific payment processing partner. Card data is stored and tokenized in a centralized, secure environment that remains accessible regardless of the processing channel you choose.
Guardian provides a secure vault that stores sensitive data off your infrastructure, dramatically reducing your PCI DSS compliance scope. Beyond vaulting capabilities, Guardian acts as a PCI-compliant proxy, helping businesses collect, store, and exchange sensitive data without ever seeing or storing it directly within their own systems.
With direct connections to all leading card networks - Visa, Mastercard, Discover, and American Express - Guardian gives businesses greater control over their tokenization and vaulting strategies. This comprehensive network connectivity is especially valuable when you want to remain payment processor-agnostic while maintaining the highest levels of security and performance.
The combination of independent operation, comprehensive network connectivity, and advanced security capabilities makes Guardian particularly well-suited for enterprises that need flexible, scalable tokenization solutions without vendor lock-in constraints.
The payment landscape has fundamentally shifted. What used to be straightforward card-present transactions have evolved into complex digital ecosystems where sensitive payment data moves across multiple touchpoints, third-party services, and geographic boundaries. For enterprise payment teams, this complexity brings both opportunity and risk.
Consider this reality: the average enterprise payment flows through 5-7 different systems before completion. Each touchpoint represents a potential vulnerability where sensitive cardholder data could be exposed, stolen, or mishandled. The cost of a single data breach now averages $4.45 million, with payment card data breaches often carrying the highest remediation costs.
This is where tokenization and token service providers become critical infrastructure rather than nice-to-have security features. But understanding how tokenization actually works, who provides these services, and how to implement them effectively requires cutting through significant technical complexity.
What is a Token Service Provider?
A token service provider (TSP) is a specialized entity that replaces sensitive payment data with non-sensitive tokens, creating a secure barrier between your systems and actual cardholder information. Think of it as a sophisticated translation service that converts valuable data into meaningless substitutes while maintaining the ability to reverse the process when legitimate payment processing is required.
The token itself is typically a randomly generated string of characters that matches the format of the original data but holds no intrinsic value. If intercepted, stolen, or accidentally exposed, tokens are useless to bad actors because they cannot be reverse-engineered or used for fraudulent transactions outside the specific tokenization system that created them.
Here's what makes token service providers particularly valuable for enterprise operations: they operate as trusted intermediaries that can securely store and manage the mapping between tokens and real payment data. This means your internal systems, third-party integrations, analytics platforms, and reporting tools can all work with tokenized data while the actual sensitive information remains isolated in a highly secure environment.
Token service providers typically offer different types of tokenization depending on your specific use case. Format-preserving tokens maintain the same structure as original payment data, making them ideal for legacy systems that expect specific data formats. Non-format-preserving tokens offer maximum security but may require system modifications to handle different data structures.
How a Token Service Provider Works
The tokenization process involves several sophisticated steps that happen seamlessly in the background of your payment operations. Understanding this flow helps enterprise teams make better architectural decisions and troubleshoot integration challenges.
When a customer initiates a payment, their sensitive card data first enters your system through whatever channel they're using - your website, mobile app, point-of-sale system, or API integration. Instead of storing or processing this data directly, your system immediately sends it to your token service provider through a secure API call.
The token service provider receives this sensitive data and performs several critical operations simultaneously. First, it generates a unique token using cryptographically secure random number generation. This token is designed to be statistically unique across your entire token population, preventing collisions or predictable patterns that could create security vulnerabilities.
Next, the provider securely stores the mapping between the original data and the new token in what's often called a token vault. This vault represents the most heavily secured component of the entire system, typically featuring multiple layers of encryption, access controls, audit logging, and physical security measures that exceed most enterprise security capabilities.
The token is then returned to your system, where it can be safely stored, processed, and transmitted just like any other piece of non-sensitive data. Your existing workflows, reporting systems, customer service tools, and analytics platforms can all work with tokens without requiring significant modifications or additional security measures.
When you actually need to process a payment, your system sends the token back to the token service provider along with your processing request. The provider retrieves the original payment data, forwards it to the appropriate payment processor or network, and returns the processing results to your system - all while ensuring the sensitive data never re-enters your environment.
This architecture creates what security professionals call "data segmentation" - a clear boundary between systems that handle sensitive data and those that don't. Most of your infrastructure operates in the token environment, while only the token service provider and payment processors work with actual cardholder data.
Who Needs a Token Service Provider?
The short answer is any organization that handles payment data and wants to minimize security risks while maintaining operational flexibility. But the longer answer reveals specific scenarios where token service providers become particularly valuable for enterprise operations.
E-commerce platforms and marketplaces face unique challenges because they often need to store payment information for future transactions, subscription billing, or marketplace payouts. Without tokenization, storing this data creates significant PCI DSS compliance burdens and security risks. Token service providers allow these businesses to maintain all their customer experience features while dramatically reducing their compliance scope.
Subscription and recurring billing businesses represent another critical use case. These companies need to process payments on ongoing schedules, handle plan changes, manage failed payment recovery, and provide customer service access to payment information. Tokenization enables all these operations while ensuring that payment data remains secure even if internal systems are compromised.
Multi-channel retailers operating both online and offline face particular complexity because payment data often needs to flow between different systems, locations, and operational contexts. A customer might save a payment method online, use it for in-store pickup, and later apply it to a mobile app purchase. Token service providers enable this seamless experience while maintaining security across all channels.
B2B companies with complex payment workflows often discover that tokenization solves problems they didn't initially recognize. When payment data needs to flow through approval workflows, accounting systems, customer relationship management platforms, and reporting tools, tokenization ensures that all these systems can operate normally without creating security vulnerabilities.
Companies expanding internationally face additional regulatory complexity as different regions impose varying requirements for payment data handling. Token service providers can help navigate these requirements by ensuring that sensitive data storage and processing occur in appropriate jurisdictions while allowing business operations to continue normally.
Perhaps most importantly, any organization dealing with third-party integrations should seriously consider tokenization. Whether you're working with analytics providers, customer service platforms, marketing automation tools, or business intelligence systems, tokenization allows you to share operational data without exposing sensitive payment information.
Key Benefits of Using a Token Service Provider
The primary benefit that drives most enterprise adoption is dramatic PCI DSS scope reduction. When your systems only handle tokens rather than actual payment data, large portions of your infrastructure fall outside PCI compliance requirements. This translates directly into reduced compliance costs, simpler audit processes, and lower ongoing security maintenance overhead.
But scope reduction is just the beginning. Token service providers enable operational flexibility that would be difficult or impossible to achieve while maintaining direct control over sensitive payment data. You can integrate with new third-party services, expand into new markets, experiment with different payment flows, and modify internal processes without constantly evaluating security implications.
Security improvements extend beyond compliance requirements. Even if your internal systems are compromised, tokenized data provides no value to attackers. This creates multiple layers of protection and significantly reduces the potential impact of security incidents. Many enterprises find that tokenization enables them to be more aggressive with innovation and system integration because the security risks are fundamentally different.
Operational efficiency gains often surprise enterprise teams. When you don't need to treat every piece of payment-related data as highly sensitive, reporting becomes simpler, customer service becomes more effective, and system integration becomes faster. Teams can focus on business logic rather than security implementation, leading to faster development cycles and more reliable systems.
Token service providers also enable advanced payment orchestration strategies that would be complex to implement securely otherwise. You can route payments through different processors based on various criteria, implement sophisticated retry logic, and optimize for cost or performance without exposing sensitive data to multiple external systems.
What Should I Look for When Choosing a Token Service Provider?
Several critical factors should guide your token service provider selection, each carrying significant implications for your long-term payment infrastructure success.
Direct Network Connections
Direct connectivity becomes essential when your operations involve latency-sensitive transactions, high data volumes, or regulated environments. Look for providers that maintain direct relationships with payment networks rather than relying on intermediary connections. This direct access typically translates into better performance, more reliable service, and enhanced security controls that matter at enterprise scale.
Security Capabilities
Your token service provider must demonstrate comprehensive security capabilities that go beyond basic tokenization. Robust tokenization methods should include format-preserving options when needed, while encryption standards like AES-256 provide the foundation for data protection. Comprehensive key management capabilities become particularly important, with the best providers allowing you to maintain control over your encryption keys when required.
Role-based access controls ensure that only authorized personnel can access sensitive functions, while detailed audit logs provide the accountability and traceability that enterprise security teams require. These capabilities aren't just nice-to-have features - they're essential components of a security architecture that can withstand sophisticated attacks.
Interoperability and Integration
Your token service provider should integrate seamlessly into your existing technology ecosystem without forcing expensive modifications or creating operational friction. Well-documented APIs and SDKs in common programming languages accelerate implementation and reduce ongoing maintenance overhead.
Support for both batch and real-time operations provides flexibility for different use cases within your organization. Some processes may require immediate tokenization, while others can benefit from efficient batch processing. Flexible token formats and compatibility with your databases, cloud platforms, and SaaS applications ensure smooth deployment across your entire technology stack.
Compliance Support
Compliance with industry standards such as PCI DSS, GDPR, HIPAA, and SOC 2 represents the baseline expectation rather than a differentiating feature. However, the depth and sophistication of compliance support varies significantly between providers.
Look for features like configurable data residency that allows you to meet regional regulatory requirements, detailed audit logging that supports compliance reporting, and regular third-party security assessments that validate the provider's security practices. The best providers treat compliance as an ongoing commitment rather than a one-time certification.
Performance, Scalability, and Availability
As your business grows, your tokenization solution must scale proportionally without degrading performance or reliability. High-throughput capabilities become critical for enterprises processing large transaction volumes, while support for both real-time and batch operations provides operational flexibility.
High availability through globally distributed infrastructure and built-in redundancy ensures that tokenization services remain accessible even during regional outages or maintenance windows. SLA-backed performance guarantees provide the assurance that mission-critical systems require, with clear remediation processes when performance standards aren't met.
Is Hellgate® Guardian a Token Service Provider?
Yes, Hellgate® Guardian is a leading independent token service provider that offers robust data tokenization, replacing sensitive data such as card numbers with format-preserving tokens. These tokens can be used throughout your systems without exposing the original data, creating a secure operational environment that maintains full functionality.
Guardian stands out as one of the only PSP-agnostic token service providers in the market. This independence allows merchants and enterprises to tokenize payment card data and manage tokens without being locked into a specific payment processing partner. Card data is stored and tokenized in a centralized, secure environment that remains accessible regardless of the processing channel you choose.
Guardian provides a secure vault that stores sensitive data off your infrastructure, dramatically reducing your PCI DSS compliance scope. Beyond vaulting capabilities, Guardian acts as a PCI-compliant proxy, helping businesses collect, store, and exchange sensitive data without ever seeing or storing it directly within their own systems.
With direct connections to all leading card networks - Visa, Mastercard, Discover, and American Express - Guardian gives businesses greater control over their tokenization and vaulting strategies. This comprehensive network connectivity is especially valuable when you want to remain payment processor-agnostic while maintaining the highest levels of security and performance.
The combination of independent operation, comprehensive network connectivity, and advanced security capabilities makes Guardian particularly well-suited for enterprises that need flexible, scalable tokenization solutions without vendor lock-in constraints.
Co-Founder & Chief of Revenue and growth at Starfish & Co. – creators of Hellgate®
Co-Founder & Chief of Revenue and growth at Starfish & Co. – creators of Hellgate®
Jens Kohnen was driven to co-start the company by the conviction that payment infrastructure should empower businesses, not bind them. Recognizing that many large organizations were locked into monolithic, opaque setups, Jens embarked on a journey to free enterprises from these rigid stacks. His mission is to enable companies to regain full ownership and monetize their flows, transforming payments from a cost center into a strategic lever for growth.
Vaulting
Feb 9, 2026
Beyond the Walled Garden: Architecting a Sovereign Payment Stack

Vaulting
Feb 9, 2026
Beyond the Walled Garden: Architecting a Sovereign Payment Stack

Vaulting
Feb 9, 2026
Beyond the Walled Garden: Architecting a Sovereign Payment Stack

Vaulting
Jan 15, 2026
Tokenization as a Service: The Infrastructure-First Approach to Data Security

Vaulting
Jan 15, 2026
Tokenization as a Service: The Infrastructure-First Approach to Data Security

Vaulting
Jan 15, 2026
Tokenization as a Service: The Infrastructure-First Approach to Data Security

Vaulting
Jan 9, 2026
Beyond the PSP: Choosing the Right Payment Tokenization Service Provider

Vaulting
Jan 9, 2026
Beyond the PSP: Choosing the Right Payment Tokenization Service Provider

Vaulting
Jan 9, 2026
Beyond the PSP: Choosing the Right Payment Tokenization Service Provider
See Hellgate CPA in action
Let our product specialists guide you through the platform, touch upon all functionalities relevant for your individual use case and answer all your questions directly.
See Hellgate CPA in action
Let our product specialists guide you through the platform, touch upon all functionalities relevant for your individual use case and answer all your questions directly.
See Hellgate CPA in action
Let our product specialists guide you through the platform, touch upon all functionalities relevant for your individual use case and answer all your questions directly.



